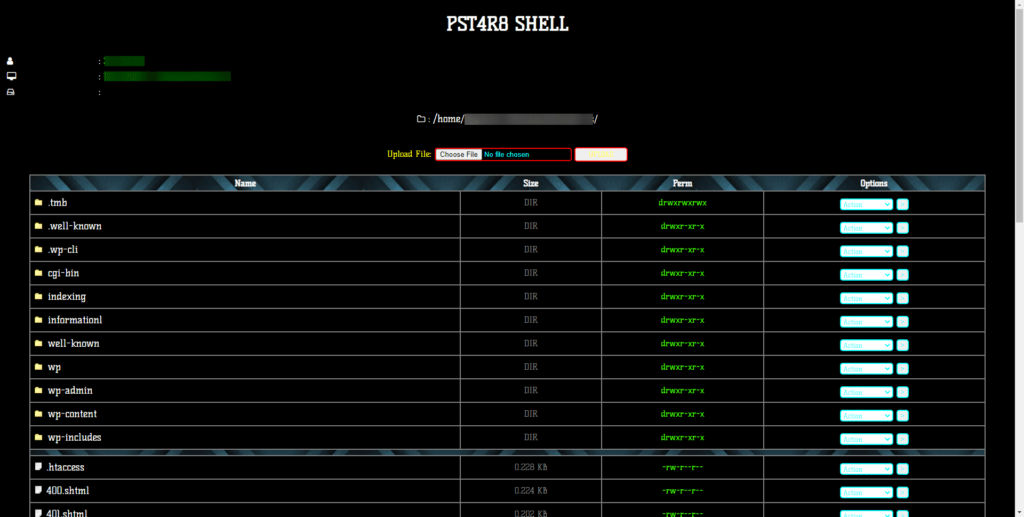
The shell contains an interesting feature that records each action performed by the script and sends to the attacker the IP address from which the request originates, as well as the file path.
So we can see all the pages that were viewed or modified from these email messages:
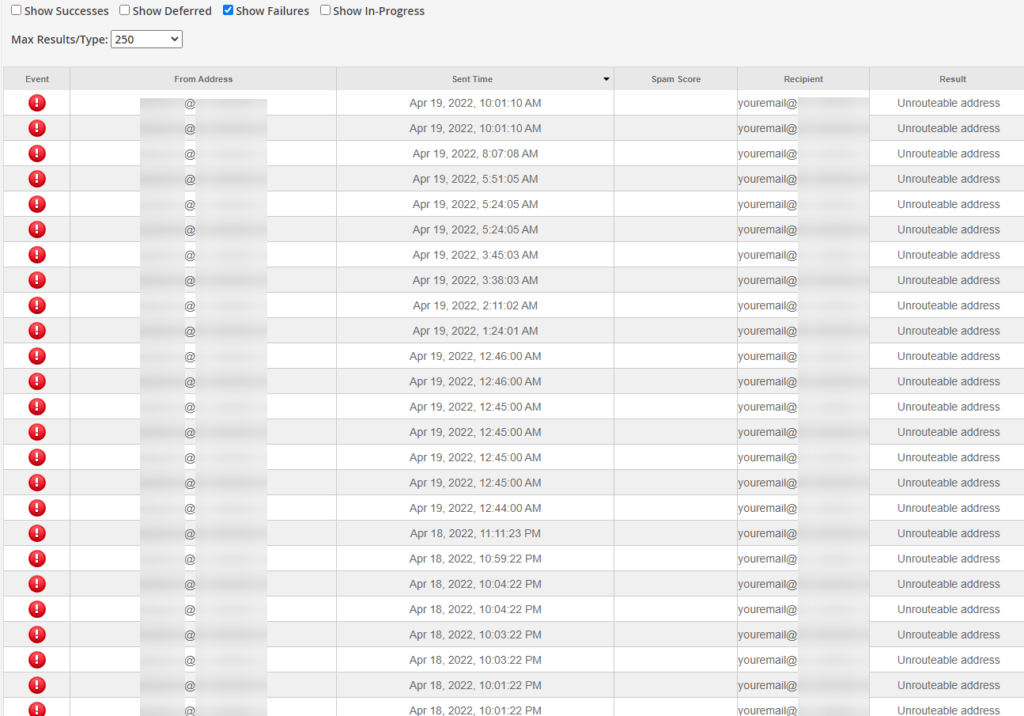
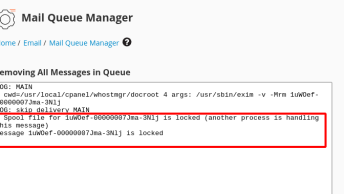
Because these emails failed, they were returned to the default cPanel account, allowing us to log in and check the emails:
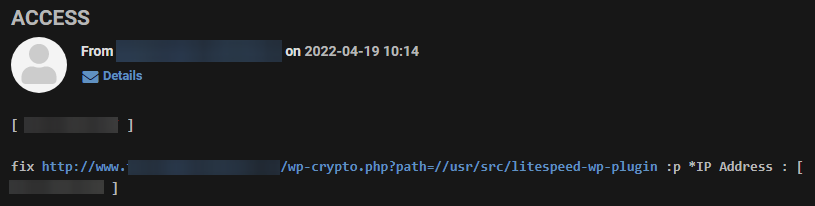
We can get a list of all pages visited from these emails and sort them into two groups:
1. Files that are owned by the user and attacker could have modified them
/home/XXXX/XXXXXXXX/.wp-cli /home/XXXX/XXXXXXXX/wp-content/themes/twentytwenty/assets/js /home/XXXX/XXXXXXXX/wp-content/themes/twentytwenty/assets/images /home/XXXX/XXXXXXXX/wp-content/themes/twentytwenty/assets/fonts /home/XXXX/XXXXXXXX/wp-content/themes/twentytwenty/assets/css /home/XXXX/tmp/webalizerftp /home/XXXX/tmp/webalizer /home/XXXX/tmp/pma_template_compiles_XXXX /home/XXXX/tmp/awstats /home/XXXX/tmp/analog /home/XXXX/XXXXXXXX/wp-content/uploads /home/XXXX/XXXXXXXX/wp-content/upgrade /home/XXXX/XXXXXXXX/wp-content/themes /home/XXXX/XXXXXXXX/wp-content/plugins /home/XXXX/XXXXXXXX/wp-content/mu-plugins /home/XXXX/XXXXXXXX/wp-content/maintenance /home/XXXX/XXXXXXXX/wp-content/languages /home/XXXX/XXXXXXXX/wp-content/maintenance/assets/images /home/XXXX/XXXXXXXX/wp-content/maintenance/assets/fonts /home/XXXX/.cagefs/var/spool /home/XXXX/.cagefs/var/run /home/XXXX/.cagefs/var/php /home/XXXX/.cagefs/var/log /home/XXXX/.cagefs/var/cpanel /home/XXXX/.cagefs/var/cache /home/XXXX/XXXXXXXX/.wp-cli/cache/core /var/cpanel/userdata/XXXX2. Files owned by root that should never be modified by a user.
/usr/src/litespeed-wp-plugin /var/tmp/alfacgiapi /var/php/apm /opt/suphp/sbin /opt/plesk/php /opt/imunify360/lib /opt/MegaRAID/MegaCli /var/run/sepermit /var/run/screen /var/run/postgresql /var/lib/spamassassin/compiled /var/lib/spamassassin/3.004004 /var/lib/spamassassin/3.004003 /var/lib/spamassassin/3.004002 /var/lib/net-snmp/mib_indexes /var/lib/net-snmp/cert_indexes /var/lib/proxyexec/cagefs.sock /var/cpanel/php/sessions /dev/shm/lsws /var/run/nscd /var/run/net-snmp /var/run/faillock /var/run/dbus /var/run/console /var/run/cagefs /usr/libexec/utempter /usr/libexec/openssh /usr/libexec/openldap /usr/libexec/mc /usr/libexec/git-core /usr/libexec/getconf /usr/libexec/gcc /usr/libexec/dovecot /usr/libexec/coreutils /usr/libexec/awk /proc/net /proc/sys /proc/self /proc/80931 /proc/171912 /opt/suphp /opt/rh /opt/liblve /opt/cloudlinux-linksafe /opt/cloudlinux /opt/app-version-detectorAnd check if any of these files owned by root have exposed sensitive information or even got is modified by an attacker.
In my case, all edit attempts were blocked, but other information that could potentially be misused such as service and PHP settings was exposed.
If you come across this malware, be sure to check all of the paths above and completely clean your WordPress website as explained in: How to clean up a hacked WordPress site (Complete Guide)
Source code: