There’s a lot of stuff out there about SQL injection attacks but there’s not much that will help you figure out how to stop these attacks from occurring.
First, let’s talk about what a SQL Injection Attack really is. Some people think it’s a virus of sorts, that is “inside your site.” Not the case. These are bot attacks by other virus-infected computers. They simply use a brute force approach of scanning URLs that take POST/GET inputs and attempt to send their own data to them.
So, how do you track these down and stop them? For web sites powered by Microsoft’s IIS, here are our suggestions:
Look at your IIS logs
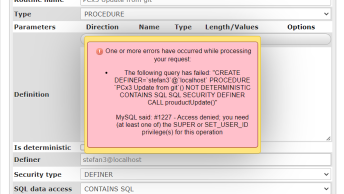
Try searching for the word “DECLARE” or “EXECUTE.” If you’ve been hit by an attack, these will more than likely show up in your IIS logs — at least for any attack that was attempted using “GET” posts.
If you do find any instances of “DECLARE” or “EXECUTE” these are the pages to start with.
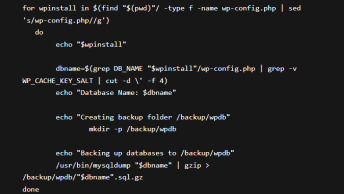
Use centralized database connection handling
Simple, make a centralized file (e.g. connection.asp if you are using ASP — see this free example) that handles all of your DB access. This way, it’s easier to make sure that you are SQL encoding your pages.
You can easily search queries for “DECLARE” and “EXECUTE” and stop the attacks dead in their tracks.
Implement a site wide solution
If you are running your own server, I highly recommend ISAPI_Rewrite 3 from HeliconTech (http://www.helicontech.com/isapi_rewrite). This is an ISAPI filter that allows you to do a variety of things, including scan URL data. This will stop 99% of attacks without changing ANY code on your site!
If you have any questions, tips, or comments, please use the comments section bellow.