A lot of Web Hosting providers only allow newer versions of TLS ciphers to be used, so only will be available:
+no_sslv2 +no_sslv3This is good security practice and should be followed on every cPanel setup. But if you have clients that use older versions of Outlook that use tlsv1/1.1 this will cause an error when they try to connect to email accounts:
SSL Connection has failed.
exim_mainlog:
exim_mainlog:2022-09-09 18:02:10 SMTP connection from [10.20.30.40]:51785 (TCP/IP connection count = 2)
exim_mainlog:2022-09-09 18:02:10 TLS error on connection from 10-020-030-040.pcx3.com (PCx3) [10.20.30.40]:51785 (SSL_accept): error:140760FC:SSL routines:SSL23_GET_CLIENT_HELLO:unknown protocol
exim_mainlog:2022-09-09 18:02:10 SMTP connection from 10-020-030-040.pcx3.com (PCx3) [10.20.30.40]:51785 closed by EOFSolution
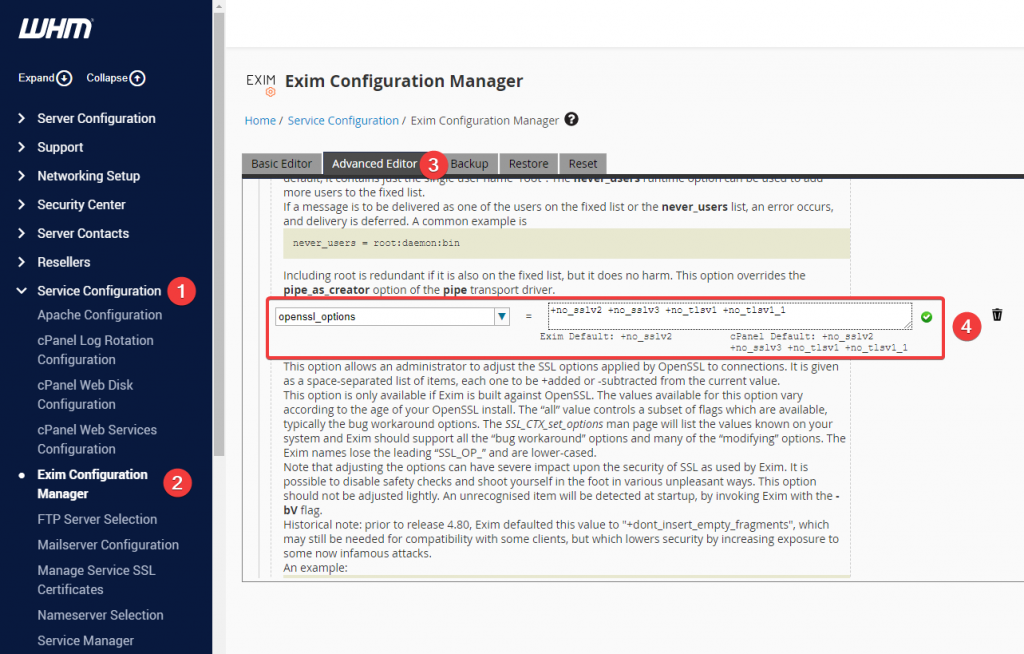
The recommended solution is for the end-user to update its email client, but if this is not an option, you can enable the use of the older TLS ciphers on cPanel from: WHM > Service Configuration > Exim Configuration Manager > Advanced Editor
Bear in mind that this is a server-wide setting and will affect all cPanel users.
Possible options:
allallow_unsafe_legacy_renegotiationcipher_server_preferencedont_insert_empty_fragmentsephemeral_rsalegacy_server_connectmicrosoft_big_sslv3_buffermicrosoft_sess_id_bugmsie_sslv2_rsa_paddingnetscape_challenge_bugnetscape_reuse_cipher_change_bugno_compressionno_session_resumption_on_renegotiationno_sslv2no_sslv3no_ticketno_tlsv1no_tlsv1_1no_tlsv1_2single_dh_usesingle_ecdh_usessleay_080_client_dh_bugsslref2_reuse_cert_type_bugtls_block_padding_bugtls_d5_bugtls_rollback_bug

![node[175421]: pthread_create: Resource temporarily unavailable 2023 08 28 12 15 344x194 - node[175421]: pthread_create: Resource temporarily unavailable](https://pcx3.com/wp-content/uploads/2023/08/2023-08-28_12-15-344x194.png)