I recently rented a tiny VPS with cpanel in order to have a better understanding of all of the cpanel files, scripts, and so on. During browsing cpanel files, I discovered that some scripts are only visible to webmail users, while others are only visible to cPanel or WHM users. I noticed that all links in Webmail go to scripts in the following directories inside /usr/local/cpanel/base/:
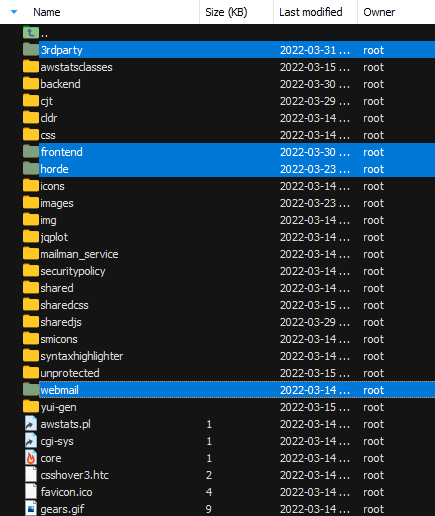
So, the next thing that I was checking is which of these directories are also cPanel users accessing, so I logged in as a cPanel user in another browser, crtl+u on the page, and searched for links to these paths.
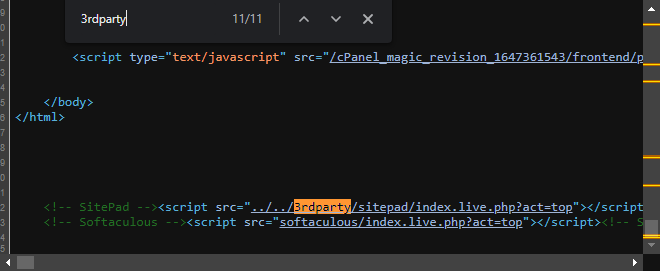
The 3rdparty folder had interesting links such as: PHPMyAdmin and phpPgAdmin:
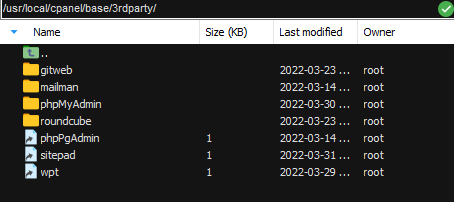
So I tried accessing them from Webmail, but they were all checking user permissions and wouldn’t let me access them from webmail.
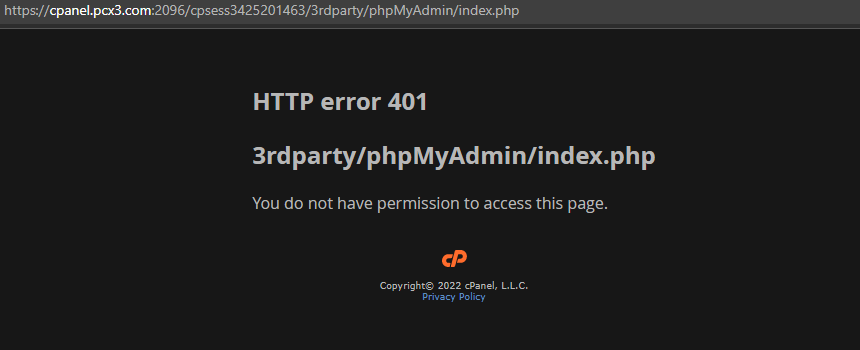
But, the sitepad link /3rdparty/sitepad/index.live.php was accessible because it’s a simple symlink to the /usr/local/sitepad/www/ directory

And this file includes the index.php file without checking any permissions:
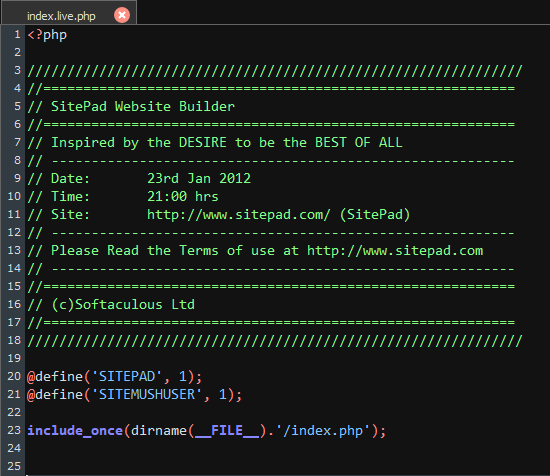
As a result in cPanel logged-in Webmail users can edit the URL parameters to access Sitepad plugin.
Steps to Reproduce
Steps to reproduce the issue in SitePad ≤ 1.7.0:
- Log into a Webmail (domain.com/webmail)
- Edit URL and add /3rdparty/sitepad/index.live.php after the cpsess_XXX part
that’s it.
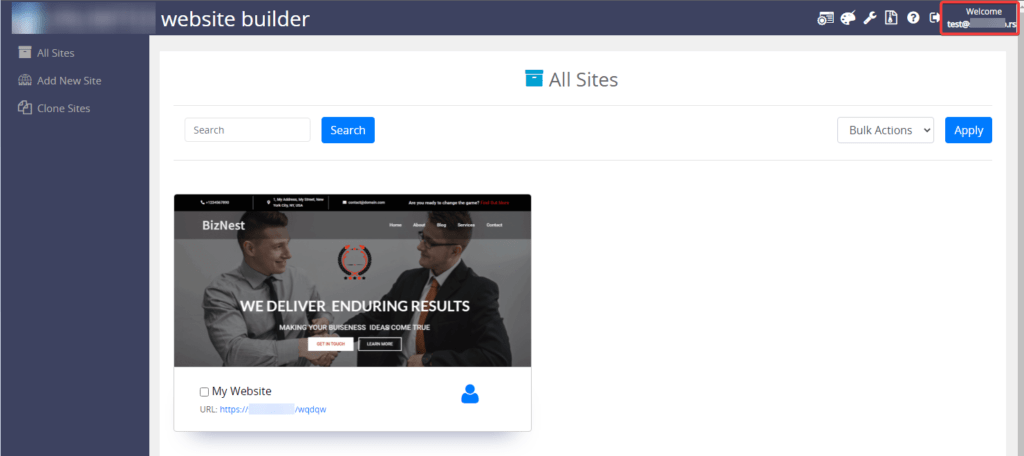
Webmail users can now edit pages or even delete entire websites.
Impact
According to builtwith, there are about 50.000 known Sitepad websites, with around 30.000 of them being vulnerable due to the use of Sitepad Page Builder as a cPanel plugin. This means that any of these sites could be accessed through hacked email accounts or former employees.
Because a single cPanel account can host many domains/websites, the majority of these sites can be used to obtain access to other websites on the account, including WordPress sites.
This extends the total number of websites and cpanel accounts that can be potentially exploited with this bug to thousands more.
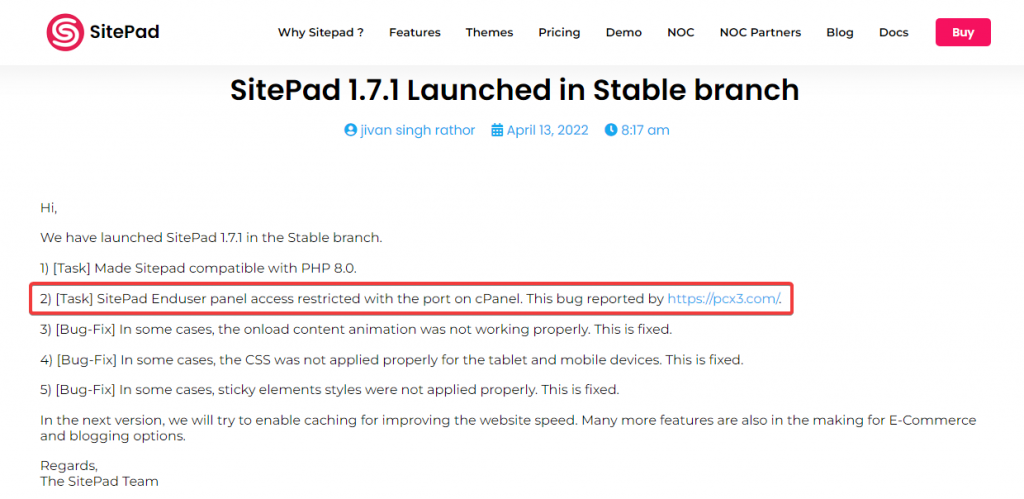
Vulnerability is Fixed in SitePad 1.7.1
I reported the vulnerability to Sitepad and the next day they notified me that they’ve started working on fixing it.
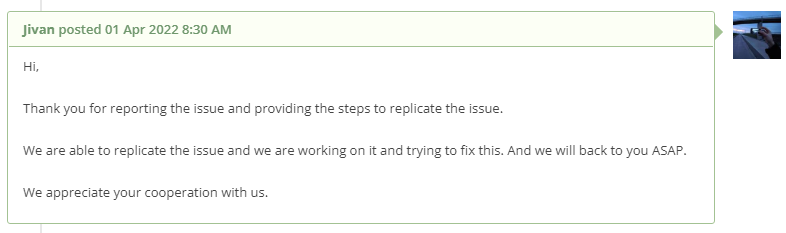
In SitePad 1.7.1 the issue was fixed:
By adding the following check inside the index.php file
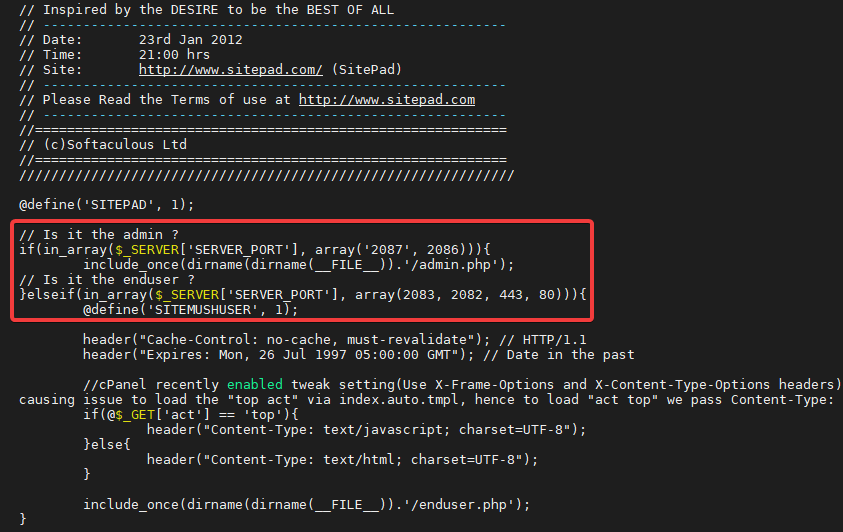
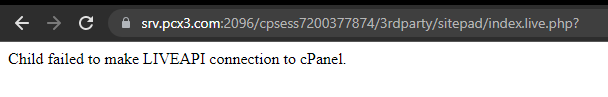
And now if you try to access SitePad from a Webmail account you will get an error message: Child failed to make LIVEAPI connection to cPanel.
Report Timeline
- 30.03.2022 – Vulnerability discovered
- 31.03.2022 – Report submitted to Softaculous – ticket ID #156870
- 01.04.2022 – Softaculous replicated the issue
- 13.04.2022 – The issue is resolved in version 1.7.1
- 01.05.2022 – Vulnerability disclosed on this blog