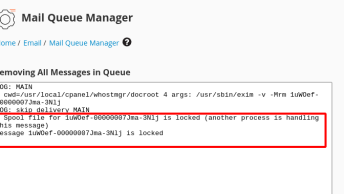
During a rutine malware cleanup a file named hax.html caught my attention.
On the outside the file was a simple “you’re hacked page” that looked like this:
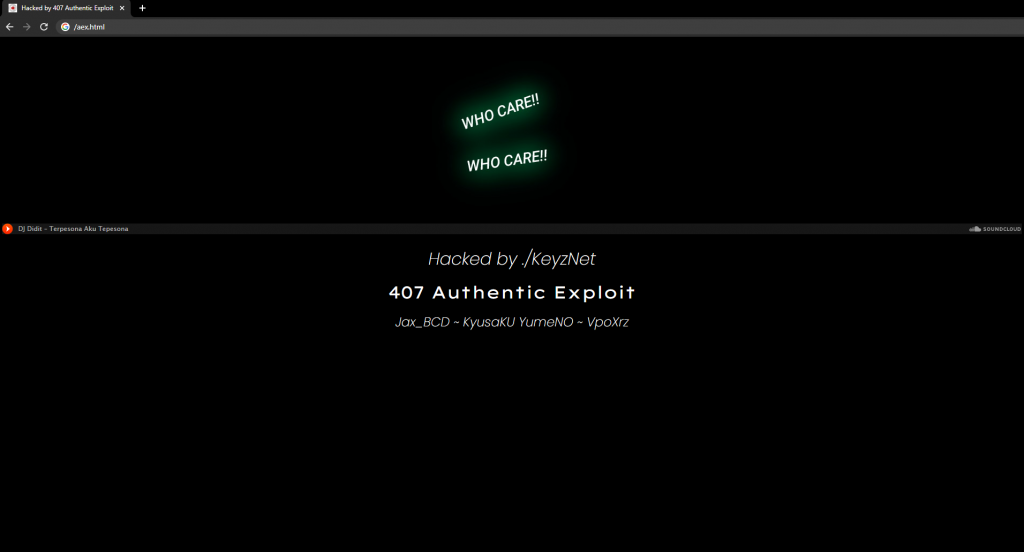
But with a POST method sent to it a nice little web shell opens up:
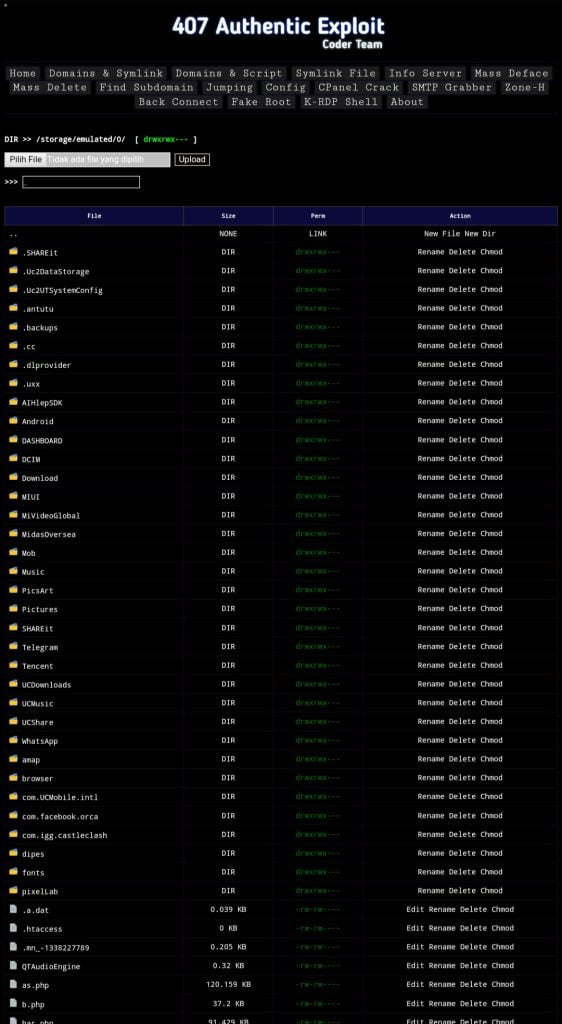
default password for this shell is: myshell
Source: github