This document only applies to the Director Requirements Download linux-2.4.18.tar.gz from and ipvsadm-1.21.tar.gz from Setup Copy linux-2.4.18.tar.gz to /usr/srcGunzip linux-2.4.18.tar.gz...
This may be a small document but for the newbie, it’s painful trying to do it through a text screen. Here’s how: at the prompt type cd /etc/xinetd.d press enter then type ls press enter and it will look like this:...
Below are some steps to clean branches from the git repository to remove the clutter. Delete a Local branch To delete the local branch in Git using the command, we can use one of the followings: # git branch -d branch_name # git branch -D...
If you have zombie processes it means those zombies have not been waited for by their parent (look at PPID displayed by ps -l). You have two choices: Fix the parent process (make it wait);Kill the parent; or live with it. Remember that living with...
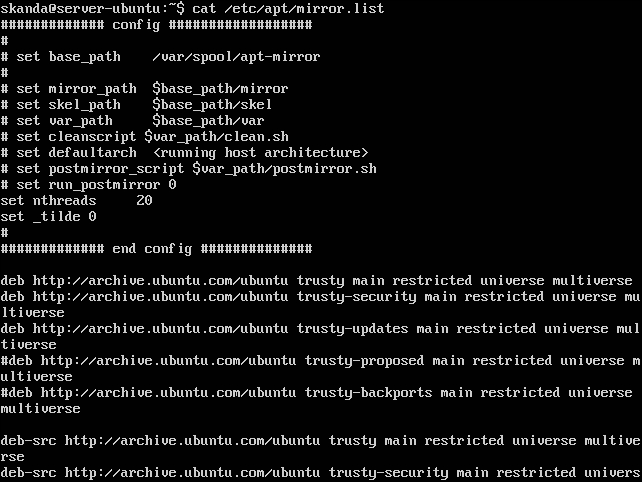
If you need to update more than one Ubuntu based Workstation or Server on a regular base, it can save you a good amount of bandwidth if you provide new packages and updates through a local Ubuntu mirror. In this document i write down the steps...
While issuing any yum command if you are experiencing the following error: # yum -y install wget Loaded plugins: fastestmirror, langpacks Existing lock /var/run/yum.pid: another copy is running as pid 13023. Another app is currently holding the yum...
First lets download the VM image from this website. Why use VM images instead of the real CentOS ico? The VirtualBox and VMware images are created in such a way that they are less in size but contains all the standard packages required for instant...
Here is how to set up a cronjob that automatically backs up a MySQL database to a file every hour. Okay, so first we need to create a new script that will be executed via cron: #!/bin/bash YEAR=`date +%Y` MONTH=`date +%m` DAY=`date +%d` HOUR=`date...
Here is a small script that will send you an email when the disk usage rises above the percentage specified by the THRESHOLD variable (90% in the example bellow). If you don’t want to step up to a full monitoring solution such as Nagios...
Here is how to restrict users to send emails to certain domains in the Zimbra mail server. 1. Open file /opt/zimbra/conf/zmconfigd/smtpd_recipient_restrictions.cf and add this line: check_sender_access lmdb:/opt/zimbra/conf/restricted_senders 2...