aaPanel is one of my favorite free hosting panels because it is lightweight and simple to use.
The panel gets regular updates, and it offers several unique features that you only get in premium panels like cPanel, but I believe the greatest obstacle to it getting more popular is that it is still just an English version of the Pagoda panel.
The Aaapanel would gain popularity among Western and European hosting businesses if it were completely separated from the Pagoda panel.
Recently, an XSS vulnerability in the Aapanel was discovered and is being exploited in the wild: A stored XSS vulnerability exists in the aaPanel security log.
Vulnerability
Aapanel has a Security log that records all bruteforce attempts and failed logins, however, if an attacker changes sections of the request header with malicious code, that code will be saved in the log file. The code will be executed the next time a website owner accesses the security log.
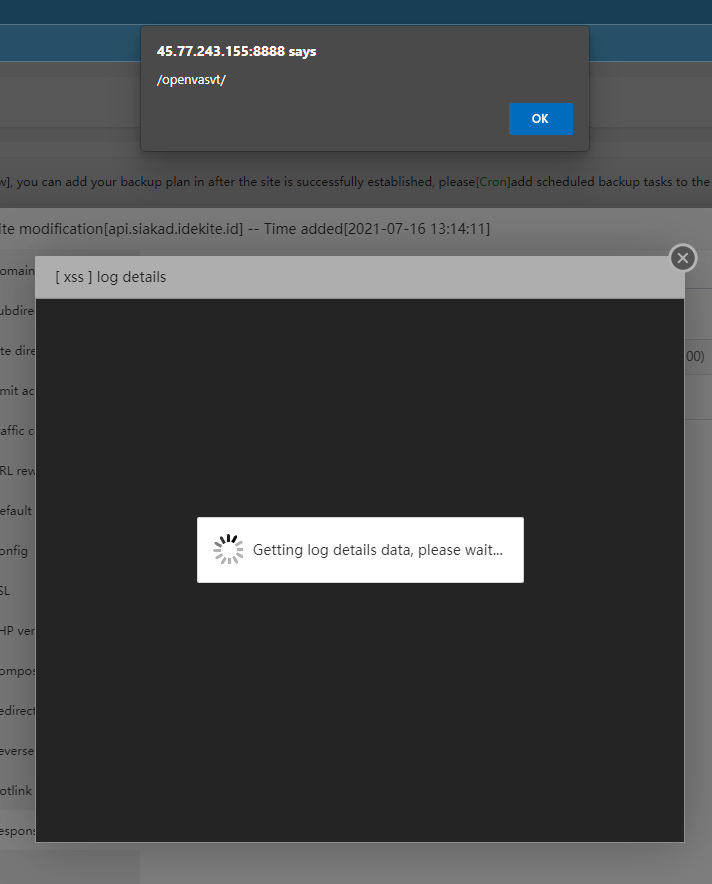
The problem was initially reported on the Aapanel forums on April 8th, and I’ll keep a watch on the changelog to see when it’s fixed.
Workaround
Until the issue is fixed and an update is available to the public, the following workaround can be done
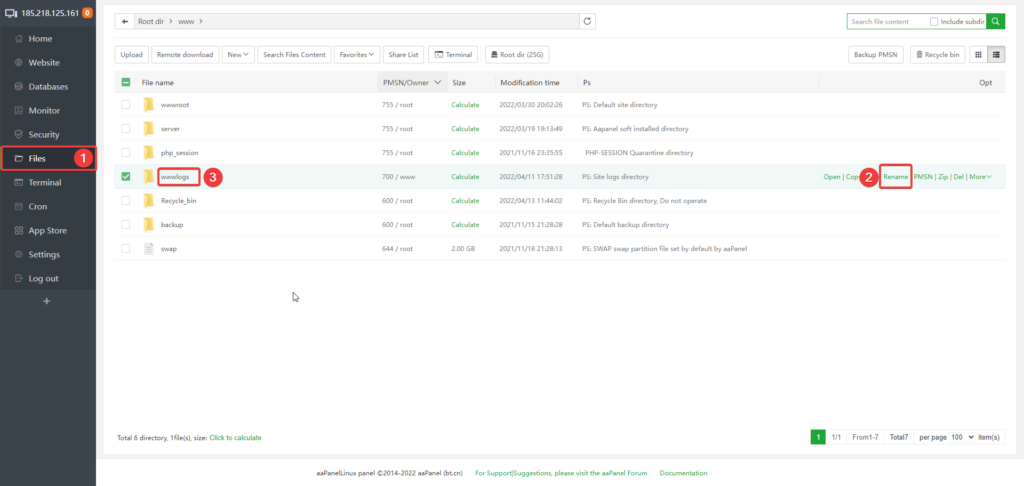
Step 1. Rename the site’s log directory /www/wwwlogs
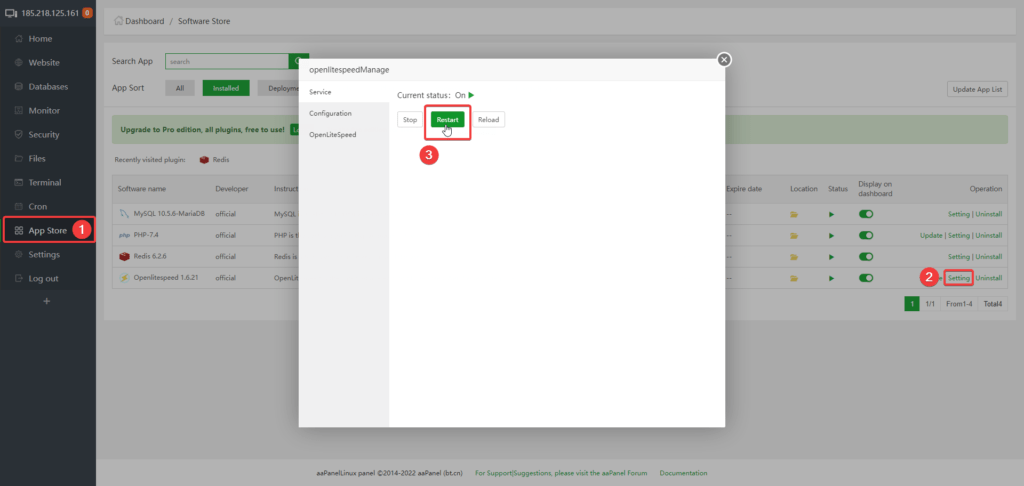
Step 2. Restart webserver after making changes
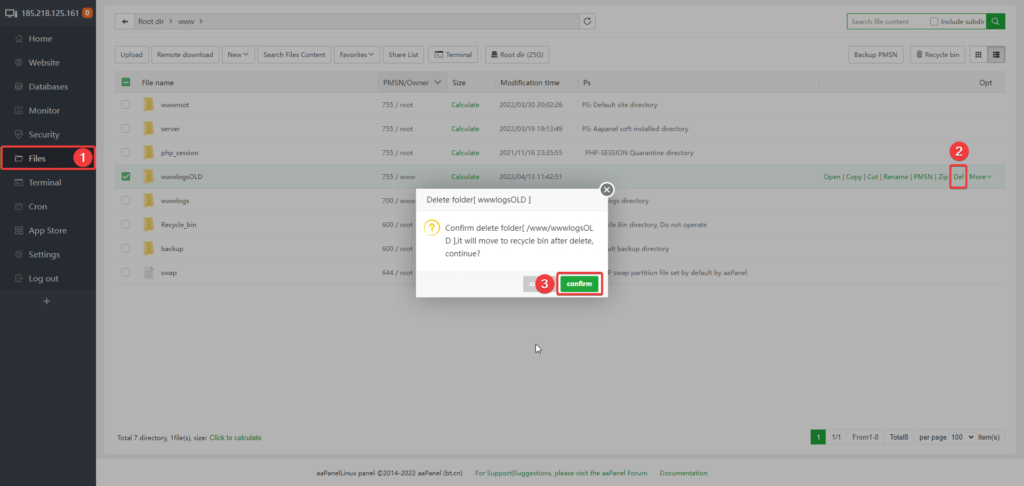
Step 3. Delete the now renamed directory /www/wwwlogs