A few weeks ago I was approached by a friend of mine, complaining about high load and CPU usage on one of his shared hosting servers (DELL) running CentOS 7, CloudLinux and cPanel. I was more than happy to take a look, and after a couple of minutes, we managed to detect the problem and resolve it.
One of the users on his shared hosting server had a security breach a few weeks ago and during that breach, a malicious script was uploaded. That script turned out to be a WSO 2.6 shell.
Most of the files that were uploaded using this shell are encoded, but upon opening their path in the browser, you can get the idea of the scripts and their general purpose.
One of the files inside the /wp-content folder named frGpoHxuaA7.php when opened directly prompts for password, and luckily the file itself contained the password:
$password = "rMJoybmXUPl"; // PasswordAfter entering the password, this page revealed:
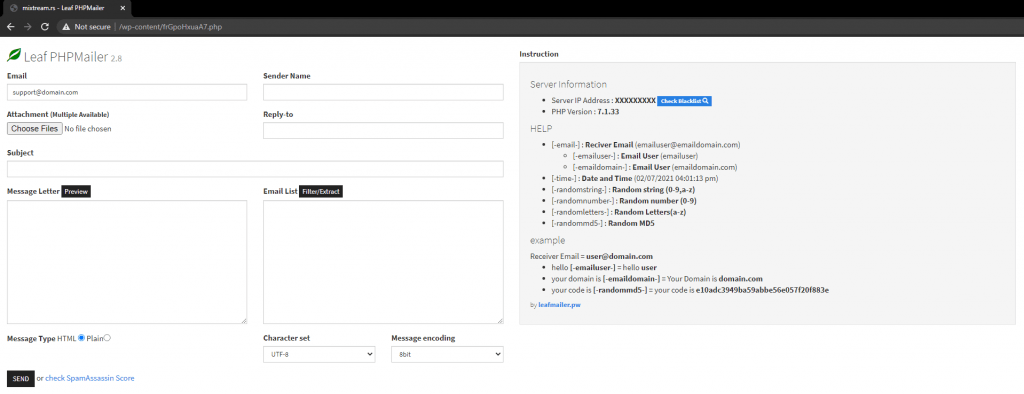
A few Google searches later, I was able to find the decoded source code and upload it in a different PHP file in the same directory.
The weird thing is, the moment that it’s run, CXS catches and puts the file in quarantine. This does not happen for the encoded version.
The file itself is a simple one-page PHP script that allows an attacker to send mass spam emails from the domain where it is uploaded.
It also comes with a few built-in tools such as:
SpamAssassin Score checker:
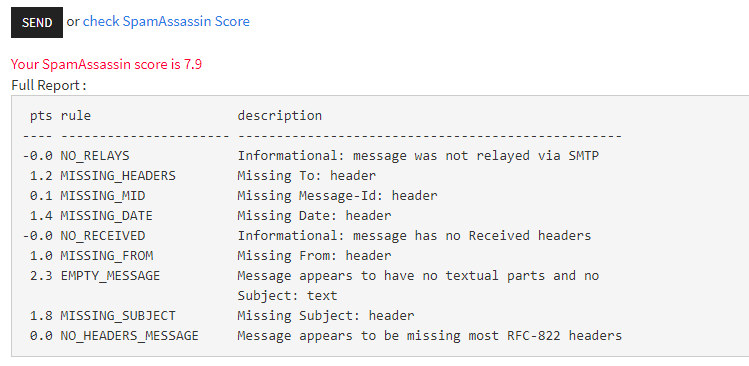
SpamAssassin is a powerfu mail filter that is used to identify spam. It is an intelligent email filter which uses a diverse range of tests to identify unsolicited bulk email (SPAM). These tests are applied to email headers and content to classify email using advanced statistical methods.
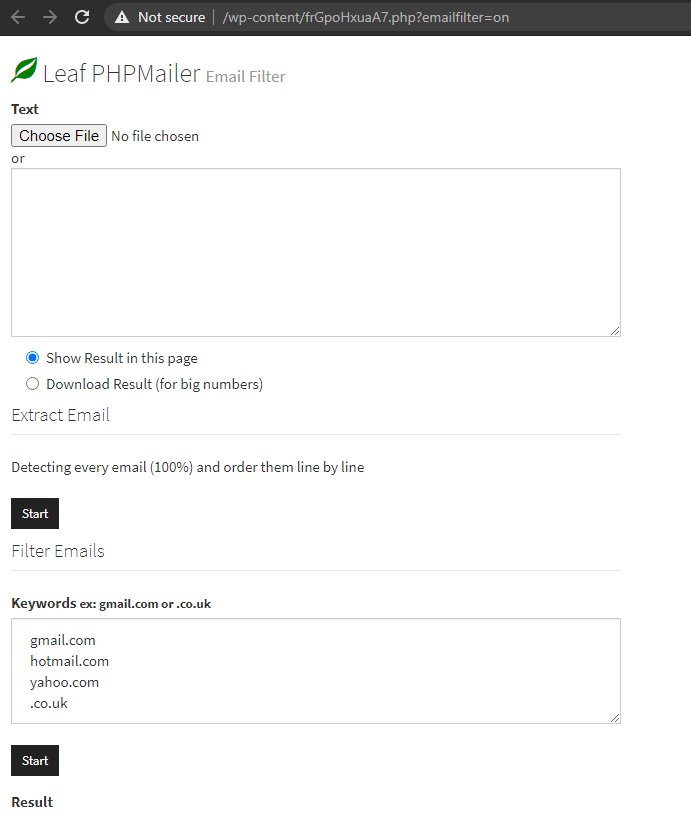
Email filter:
RBL blacklist checker:
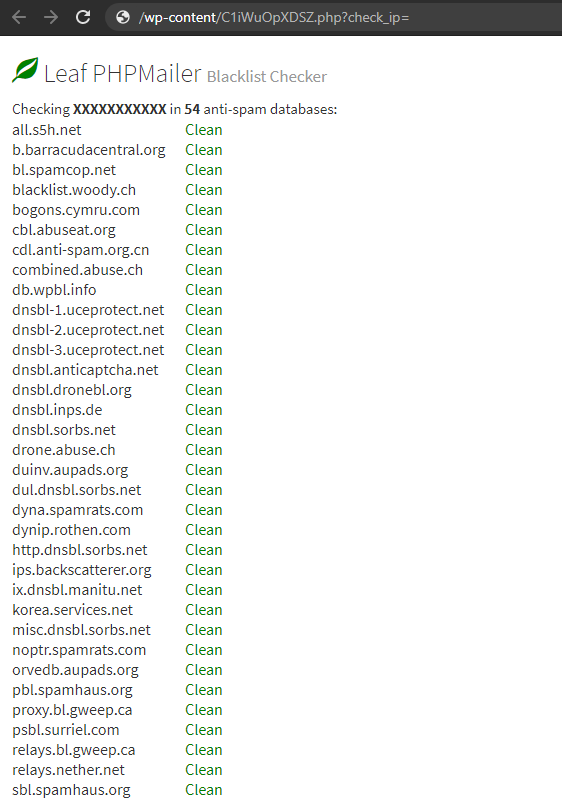
The blacklist check will test a mail server IP address against 54 DNS based email blacklists (also known as Realtime blacklist, DNSBL or RBL).